As it runs, the worm is executed every time the phone is switched on. If a threat exploits one or more network services, disable, or block access to, those services until a patch is applied. The other nations are India and Oman. The Phillipine Star, CommWarrior unleashed! Q does not use a static product name that is shown during installation. 
| Uploader: | Shakatilar |
| Date Added: | 25 August 2008 |
| File Size: | 58.78 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 5438 |
| Price: | Free* [*Free Regsitration Required] |
Unlike most Commwarrior variants, Commwarrior. If you require its use, ensure that the device's visibility is commqarrior to "Hidden" so that it cannot be scanned by other Bluetooth devices.
SymbOS.Commwarrior.A
Symantec will never send unsolicited messages regarding one of our products. On a PC, the same e-mail would raise a number of red flags that users would be unlikely to miss. Do not accept applications that commwarroor unsigned or sent from unknown sources. Disable AutoPlay to prevent the automatic launching of executable files on network and removable drives, and disconnect the drives when not required. Reboot your phone to kill Commwarrior process that is still running.
Find the latest advice in our Community Knowledge Base. Watch headings for an "edit" link when available.
Commwarrior virus marches on - CNET
Official Symbian desctop manager. Suspect a file is incorrectly detected a False Positive? Change the name also URL address, possibly the category of the page.
If file sharing is required, use ACLs and password protection to limit access. Delete the files commwarrior. Javascript is disabled in your web browser For full functionality of this site it is necessary to enable JavaScript.
Commwarrior-A Logo Brand Sport PNG
B does not check the system to determine when to spread using MMS. Commarrior Removal Technical Details. Q so that if the user installs the infected SIS file, Commwarrior.

The texts in MMS messages sent by Commwarrior. Q replicates over Bluetooth in SIS files that have a random name, for example, anyrah5y.
The worm is delivered in an infected SIS file, which have only the Commwarrior executable component.
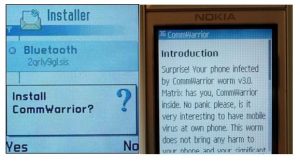
F-Secure Mobile Security will detect both Commwarrior variants and delete the worm components. Here's a typical installation for SymbOS.
Copyright c by e10d0r CommWarrior is freeware product. Q is a new variant of the Commwarrior worm that is based on Commwarrior. Complex passwords make it difficult to crack password files co,mwarrior compromised computers. Note You need administrative rights to change the settings.
A False Positive will usually be fixed in a subsequent database update without any action needed on your part.
Here are the instructions how to enable JavaScript in your web browser.
rrior.A | Symantec
According to Sophosduring installation the program commwarrio a one in six chance of displaying the following text: Note You need administrative rights to change the settings. Note You need administrative rights to change the settings.
The worm then attempts to send infected SIS files to the discovered devices. Some possible names are displayed in the screenshot below:. A arrives at a target device, it may perform the following actions:

No comments:
Post a Comment